Security automation is the process of using tech to back up your site, scan for security weaknesses, and carry out related tasks—without any manual work involved.
When a security concern materializes, you need to squash it fast before it affects your company's finances and its reputation with customers. Luckily, with Zaps (what we call automated workflows at Zapier), you can watch out for and address those risks reliably, quickly, and in compliance with SOC 2, SOC 3, and CCPA.
If you're ready to be more proactive about protecting your digital assets, keep scrolling—below I'm sharing some automated workflow ideas and ready-to-use templates to get you started.
Always talk to your security team or expert to keep your company, employee, and customer data safe.
Skip ahead
What is security automation?
Security automation is the use of security automation tools to prevent cloud security and cyber security threats by automatically detecting, investigating, and responding to them before they do real harm.
As businesses scale and teams spread out across the globe, keeping tabs on everything, from devices to software to cloud infrastructure, can start to feel like a game of whack-a-mole. And when you're manually managing hundreds of tools across a hybrid environment, it's impossible to scale securely. This leaves way too much room for error when it comes to business safety.
But with security automation in place, you can securely connect your company's tools, processes, and infrastructure. That way, your teams can handle the routine security tasks that ladder up into stronger threat protection—at scale and in real time. That can include anything from flagging suspicious activity to monitoring for fraud automatically. (All without burning out your IT and security teams, of course.)
That shift means teams spend less time reacting to noise and more time proactively protecting against real threats like malware, phishing attacks, unauthorized access, and data breaches.
Security automation aims to solve:
increased security breaches that are too fast and too complex to catch manually
poor incident response times, where delays can turn minor issues into full-blown crises
difficulty enforcing security policies across cloud apps, remote teams, and hybrid environments
an increase in false positives that bury real threats in a sea of alerts
How does security automation work?
Security automation turns manual, repetitive tasks into automated workflows that keep your systems more secure. Instead of reacting to every alert or combing through logs, you can use automated security tools to do the hard work for you.
Here's how that typically works behind the scenes:
Threats are detected in real time: From unusual login attempts to configuration errors, automation constantly monitors your systems for potential risks. The right system monitoring tools can flag these threats the moment they appear.
Issues are triaged and sorted: Once something is flagged, it's sorted and scored automatically. Rules or even AI tools (think machine learning models) can determine whether it's a real threat or just noise.
Pro tip: Check out Zapier's AI tools to handle tasks that go beyond rule-based automation. Machine learning models can analyze system performance and detect anomalies, allowing security teams to focus on high-impact tasks.
Security events are responded to immediately: When an issue or unusual activity is flagged, automated workflows jump into action right away. They log incidents, notify your team, or kick off responses to contain any issues.
User access and permissions are streamlined: When someone joins or leaves a company, automation security can cover tasks like prompting users to enable multi-factor authentication (MFA) or revoke app access securely.
Security policies are consistent across all apps: Automation ensures your security policies are applied uniformly across every app, platform, or tool your organization uses. This helps eliminate gaps or oversights that could lead to vulnerabilities.
Compliance and logging happen in real time: When a response is triggered, security automation tools can record the event, then log what triggered it in your database, what actions were taken, and when. While these logs can be used for conducting audits and compliance purposes, they also help teams improve incident response processes over time.
Pro tip: Use Zapier Tables—a database tool built for automation—to create secure, reliable data systems for your most important information.
All in all, security automation aims to help teams cut through the noise and focus their time and attention on higher level security tasks that actually require human approval.
Types of security automation tools
While different types of security automation tools can be used to protect your company, here are a few of the most popular tools you can (and should) use in tandem:
Extended Detection and Response (XDR) is a security tool designed to detect and respond to threats by analyzing data across endpoints, networks, and multicloud environments, using built-in AI to speed up decision-making.
Security information and event management (SIEM) is a set of tools and services that logs events data, threat intel, and vulnerability feeds from multiple systems to support compliance and provide detailed analysis. It provides real-time monitoring and automatic alerts.
Security orchestration, automation, and response (SOAR) is a set of programs focused on automating handling and responding to security events once an alert or condition has been triggered. It covers processes like vulnerability management and security incident responses.
No-code automation tools connect the different apps in your security stack, allowing you to build automated workflows that trigger based on specific conditions or events. That might include sending real-time alerts when a system fails or logging key events for compliance.
Did you know? Zapier is the only AI orchestration platform that combines the security oversight IT demands with the speed your business teams need.
Security automation vs security orchestration
If you've heard the terms "security automation" and "security orchestration" used interchangeably when using automation tools, it's easy to get confused. While often treated as the same thing, there are a few key differences between the two.
Security automation (known more broadly as workflow automation) is the act of automating individual tasks within security processes without humans stepping in. An example might include creating a high-priority ticket in Jira whenever a security tool like Intruder detects a threat.
Security orchestration (known more broadly as workflow orchestration), on the other hand, is the bigger picture. It combines all those automated tasks together into a complete end-to-end process, like detecting threats, notifying the right teams, and then adding reports to a database.
For example, say you want to proactively scan for security vulnerabilities across your infrastructure each week. With security orchestration in place, you can:
Automatically trigger a weekly scan using a tool like Halo Security or Intruder
Convert any detected vulnerabilities into high-priority Jira issues or Zendesk tickets
Send an alert to your IT or security team in Slack or email
Log results in a centralized spreadsheet or database for tracking and auditing
Flag critical vulnerabilities for immediate review or follow-up actions

Each of those steps can be automated individually (and that would be security automation) but orchestration means they happen in the correct order, with the right data passed between systems with no confusion in between.
Automated security with Zapier
Now that we've covered the essentials of security automation, it's time to take your security strategy to the next level with Zapier.
Zapier is the most connected AI orchestration platform—integrating with thousands of security automation tools like Datadog, Okta, Intruder, and PagerDuty.
With automated workflows called Zaps, you can securely connect your IT apps to the rest of your tech stack and streamline your IT processes.
Security is non-negotiable at Zapier. With enterprise-grade encryption, real-time threat detection, and granular permissions, you're always in control—and your data is always secure. Zapier is GDPR, SOC 2 Type II, and CCPA compliant, with built-in controls that give you full ownership over your data.
Back up your site and important information
While we often think of cyberattackers as those that try to extract information, some will try to alter, add, or delete data. That's why it's crucial to have a backup version of your site that's always up to date.
With Zapier, you can automatically back up documents shared between different cloud services or store backups of all the blog posts you create in WordPress. You can rest easy that the parts of your site that take the most time to create are protected from intentional attacks or unexplained crashes.
Create Firebase / Firestore cloud documents for new or updated Google Sheet rows
Create Google Sheets rows for new documents in Firebase / Firestore collections
Add new Snowflake rows to Google Sheets as spreadsheet rows
Similarly, you might use identity access management (IAM) tools like Okta or Google Workspace Admin to give users secure and controlled access to your system. But aside from everyday access, you may also want a backup of your user directory for both employees and customers. These Zaps create new rows in Google Sheets or Zapier Tables for new events and users in your IAM app.
Log new Okta events by creating corresponding rows in Google Sheets
Log new Microsoft Entra ID users by updating corresponding records in Zapier Tables
Update Google Sheets rows when Google Workspace Admin users are updated
Spreadsheets are great for storing information, but they're not built for acting on it quickly. For a more dynamic automated system, try Zapier Tables. With it, you can store data, trigger automations, and connect all your organization's apps and workflows to your spreadsheet data.
Scan for security weaknesses proactively
A reliable backup is a great start, but it's not all you need to keep your business data safe. You also need to take full stock of your website and make sure every element is fully secure against outside attacks.
There are plenty of reliable security tools that can help shore up your online defenses. Tools like Halo Security and Intruder, for example, can save you enormous effort by proactively flagging issues and running scans automatically.
And with these Zaps, you can run security scans weekly and turn new threats into Zendesk tickets or Jira issues. That way, your security team has help identifying and responding to security risks as soon as they appear.
Create a Zendesk ticket when Intruder detects a new issue
Create issues in Jira Software Cloud for new Halo Security issues
Pro tip: Automate your security operations even further with Zapier Agents. These AI-powered agents can perform actions like running scans, logging issues, and notifying the right team—across our ecosystem of nearly 8,000 apps.
Bring incident activity into your server monitoring dashboard
Your server monitoring tool already keeps tabs on your infrastructure's performance, but what happens when incidents get reported in other security tools?
By integrating external incident reports directly into one monitoring dashboard, your team gets instant visibility into issues, no matter where they're first detected. But of course, manually tracking every minor event across multiple apps doesn't scale (or pay off in terms of reliability).
Instead, you can use these Zaps to automatically push critical security events, like a triggered PagerDuty alert or an incident logged in incident.io, straight into tools like Datadog. That way, your security teams get a full overview of every incident.
Get new Uptime.com check alerts as metrics in Datadog
Post new metrics in Datadog for new or updated PagerDuty incidents
Post new metrics in Datadog when new incidents occur in incident.io
Send alerts to the right team
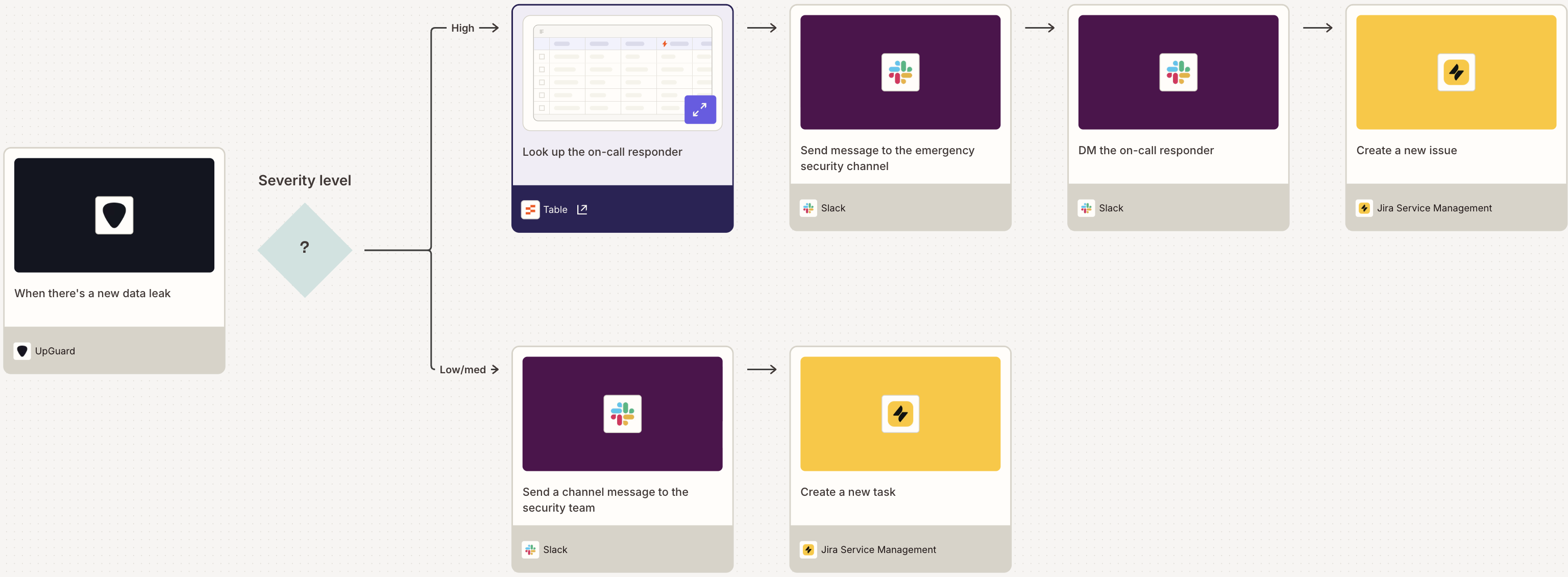
One key to protecting your digital assets is reacting quickly to important developments. It's crucial to send notifications to your customers about activity in their accounts or alert your team of new security issues. But no matter how big your team is, you can't stay on top of every breach or leak or blocked page visited.
Unless you're using automated workflows. These Zaps can alert you immediately to a security problem in your infrastructure. Use tools to scan for vulnerabilities and cybersecurity weaknesses, then send real-time notifications with Zapier's Slack or Teams integrations. That way, your team can stay on top of threats without being glued to your security tool dashboards.
Receive Microsoft Teams channel messages for new or updated alerts in Acronis
Send Slack messages for new incidents on PagerDuty
Send Slack channel messages for new identity breaches in UpGuard
Get Gmail notifications for new data leaks in UpGuard
Send Microsoft Teams channel messages for new DNSFilter blocked page form submissions
Pro tip: Use a paths step to separate high-severity incidents from low- and medium-severity ones. For example, you can route critical leaks to an on-call responder while creating a follow-up task for lower-risk leaks.
Create and store complex passwords securely
Despite knowing it's a terrible idea, so many people use the same or variations of the same password for almost every login they have. For business owners and employees, this may mean they use the same password for their Target account as their entire employee database.
This poses a massive security issue, as a single member of your organization could put your entire digital system and database at risk. Password managers like LastPass or 1Password can help prevent this by automatically developing complex passwords for each user and each site, then storing them securely. And not only do these tools keep you secure, but they're accessible; people can use them across multiple devices.
Even better, LastPass integrates with Zapier, which lets you automatically convert users in your most-used apps into LastPass team members. If you're worried about security standards for freelancers or contracted site developers, these automated workflows are a great solution.
Add new BambooHR employees as LastPass team members
Add LastPass users from new Gravity Forms submissions
Add LastPass users from new Google Sheets spreadsheet rows
Continually monitor for fraud
Unfortunately, it's common for people to place false orders that could hurt your business. Fraudulent credit card transactions can be devastating for small businesses, so detecting threats early can save you an exorbitant amount of time and money. Tools like IPQualityScore, iDenfy, and IdentityCheck monitor for fraud on every purchase, protecting your business in the process.
You can use the Zaps below to send new customer orders or inquiries to an authentication app and check for known signs of fraud before you ever fulfill an order.
Verify and update new Stripe customers with IPQualityScore
Verify email in IPQualityScore for every new message in Facebook Messenger
Create identity verifications in IPQualityScore for every new purchase in WooCommerce
Validate phone numbers in IPQualityScore when new or updated contacts appear in Google Contacts
Lookup IP address reputations through IPQualityScore with new updates to Google Sheets rows
The secure way to secure your business
Your website and digital presence are essential to your brand, and it's likely the web is where customers interact with you most. Just as you would make sure you had high-quality locks on your doors and a surveillance system around your brick-and-mortar store, it's crucial to take steps to continually protect your digital assets, too.
That's where security automation and security orchestration come in. Instead of manually juggling individual security tasks, orchestration ties all your security tools and processes together, handling threats seamlessly in the background. It flags critical issues immediately, coordinates responses automatically, and ensures your security infrastructure works as one integrated system.
Related reading:
This article was originally published in April 2021 by Ana Gotter. It was most recently updated in November 2025 by Steph Spector.